Protection Services
COMING SOON: Our Unique Value Proposition
Radio analytics
in up to
1000 m height
Pentesting
Radio coverage measurement

Penetration testing
Wi-Fi 5 & 6
Handshake cracking
Robustness assessments
Information Gathering


COMING SOON: Penetration testing
Sub-GHz Devices
(RFID/NFC/IR, ...)
Intercepting and analyzing sub-GHz
waves, e.g. for cars, garage doors,
IoT devices, and alarm systems
Emulating remote controls
Testing access control systems
COMING SOON: Radio Coverage Assessment
Mobile networks and Wi-Fi
Testing signals
from various wireless protocols,
including LTE and Wi-Fi 802.11 (a/b/g/n/ac/ax).
Large-scale analysis of radio coverage.


Penetration testing
Sub-GHz Devices
(RFID/NFC/IR, ...)
Intercepting and analyzing sub-GHz
waves, e.g. for cars, garage doors,
IoT devices, and alarm systems
Emulating remote controls
Testing access control systems
Our services
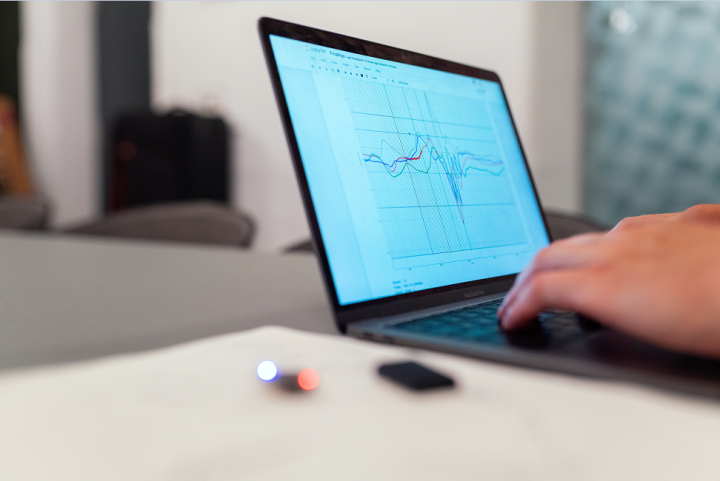
Radio pentesting
Pentesting of
radio equipment
Analysis of
radio coverage
Attack mitigation
Mitigation
of radio attacks
Prevention
of unauthorized access
Schedule
On demand
Continously
